With the increasing number of networking functions and near-field communication methods, there are more and more places where cars can be attacked. To break through the defense line of a car, what can I start with? How do car manufacturers and suppliers prevent intrusions? After analyzing the crack cases one by one, the following is a summary.

The invasion of the car seems to have come to an end, but the problems behind it are far from being.
In this year's case, ModelS was exposed by KevinMahaffey and MarcRogers, and BYD's announcement of the cracking process in 360, the contents of the announcement, all mentioned a very important premise, that is, "physical contact." Because for cars, only remote and reproducible attacks can really pose a threat.
The reason is obvious. Although physical contact attacks have caused great harm, the implementation is very difficult, time-consuming and laborious. For real hackers who are pursuing profits, the payout ratio is too large. Long-range attacks are flexible, and the probability of being caught is much lower.
It must be stated that physical contact attacks and remote attacks here refer to the means used in the attack. Physical contact is an indispensable process when studying vulnerabilities. It is not possible to prove that a vehicle cannot be attacked remotely on the basis of "physical contact."
From the perspective of the Internet, there are loopholes that are not terrible, because as of now, no system can be said to be absolutely secure. Vulnerabilities naturally have measures to plug loopholes, protect vulnerabilities, and reduce the existence of vulnerabilities.
So, in this year's case, what are the vulnerabilities exposed by vehicles? Let's take a look at the case to see its culprit.
Chrysler Incident
In the remote control incident of Chrysler, Uconnect eventually became the back pot, becoming the entrance to Miller and Valasek taking over the vehicle control system. But the real reason for the brakes and transmission of the vehicle is not just Uconnect. This point is also a bit of a name in the previous article:
In order to prevent hackers from accessing a non-essential network and then "breaking into" the internal network of the system, a general security expert will install a "air gap" between the two lines. However, on the "black" Jeep Cherokee, there is no gatekeeper between the systems that control the operation of the vehicle. Therefore, in combination with several other security vulnerabilities found, Charlie and Chris discovered the connection between the vehicle control system and the Uconnect system (which dominates the instrument entertainment unit). A loophole in the SIM card, combined with other attacks by "hackers", turned the remote control that could have been theoretically possible into a naked reality. It can be concluded that there are two reasons for this incident: First, Uconnect provides an interface for wireless access vehicles, and second, there is no isolation between the Uconnect infotainment system and the vehicle control system. After entering Uconnect, it is equivalent. Fish into the sea, unimpeded.
After the vulnerability broke out, Chrysler had no choice but to recall it because it could not be remotely updated. The benefit is that the severity of the vulnerability event has caught the attention of NHTSA and may have contributed to changes in information security standards.
Summary : The drawbacks are that the infotainment system is not in place, the isolation between different systems of the vehicle is not in place, the remote vulnerability cannot be updated, the OTA upgrade, the isolation gateway between the vehicle internal control system and the infotainment system is provided, and the verification means and information entertainment are enhanced. The security measures of the system itself are all available means.
Universal Onstar and other car networking service apps with the same vulnerabilities
SamyKamkar opened the vulnerability of the car networking service app of four car companies and a post-installer with the Ownstar box. Principle We have already made it clear that Ownstar will scan the WiFi network that the mobile phone has connected to and pretend to be one of them. Once the mobile phone is connected to the WiFi network, it can read the verification information of the App and use the authentication service to use the Internet of Things service APP. All the features provided, lock unlocking, vehicle positioning, remote start and more.
In this process, the loopholes are :
1. The WiFi network connected to the mobile phone can be arbitrarily scanned and read, and the WiFi with the same name is automatically connected (the problem exists in the mobile phone)
2. Only one verification information, after passing the verification, there is no secondary verification, and the verification information will not be updated, once for a lifetime benefit.
This can be attributed to the same case in the 360 ​​case of the car cracking incident witnessed by the previous car cloud, and the lack of verification means. As for this method, it can crack more cloud service permissions, and even let the cloud command priority is greater than the local service. Kamkar has not tried it, and we don't know.
The difference with the Chrysler incident is that the app offers more than just an entry. Because of the content of the service, the App itself can communicate with the part of the vehicle's control system and obtain control rights. Therefore, once the App has problems in the permission setting and verification means, these control rights are sent in white.
This problem can also be extended, for example, vehicles now support remote control of basic functions from smart watches.
Summary: These car networking services have no problems in themselves, and they do bring convenience to consumers. They cannot be decommissioned because of waste. Therefore, the key is to strengthen the security measures of the app: the encryption method is enhanced, the verification means such as SMS verification and strict authority are added. Settings.
Control Chevrolet Corvette with OBD
Like the Chrysler incident, in this case, there are two "Prisoners", one is the OBD device of MobileDevices, and the other is the Corvette vehicle CAN bus.
The OBD problem of MobileDevices is that the developer mode uses the same key to allow hackers to easily obtain the highest privilege. The second is to send commands through SMS. The SMS does not require any means of verification to open the door for hackers. However, the solution is not so difficult. It can be updated through OTA. One is to change the permission settings, and the other is to increase the whitelist of SMS control. Only the command can be sent via the specified mobile number to take effect.
Summary: Fundamentally, the loopholes in OBD are very similar to those of Chrysler's Uconnect, because they can be networked and have security holes, which gives hackers a chance, but the root cause is also the security policy setting of the CAN bus. For the vehicle control function without increasing the level of verification, the hacker can be driven straight.
Wireless key unlocking the door
The way RollJam breaks into the door is known. By listening to and storing the password that the wireless key uses to unlock it, you can use it to open the door.
On the Hackpwn of 360, Car Cloud consulted about how SamyKamkar handles the different passwords used to unlock and lock the door. Kamkar's explanation is that some vehicles use the same password, but with different commands, let the car know whether to unlock or lock, and some vehicles use different passwords. RollJam recognizes the password and the corresponding command and only stores the password for unlocking. Moreover, the number of stored passwords can be freely set, and one can be stored or four.
This vulnerability was eventually attributed to the chip issue by SamyKamkar. Because the success of his use of RollJam to attack Cadillac's new car is that there is a key system on the Keelop chip used in this car, which sets a very short period of validity for the key. Once the time is over, the key will be time-sensitive. This type of eavesdropping can be blocked.
Summary : The timeliness of setting a password makes it impossible for people to get a password.
Car ignition anti-theft system
Unlike wireless key unlocking, the problem with the ignition anti-theft system is that the password component is deciphered, and the way the password is set makes it easy to read and write the contents of the password.
In addition to replacing the new cryptographic protocol, there is no other way. The good news is that in the new models, more and more use of keyless start. Of course, there is a keyless start-up loophole that requires attention.
Summary :
From these cases, it can be seen that the car can be attacked: one is the entrance, and the other is the internal security strategy. OBD, Uconnect, or the App itself just provides an entry. Insufficient security measures in the entrance itself, too much open authority gives hackers opportunities, and the setting of the vehicle's internal security strategy is fundamental, and it also requires the car companies to think about it.
But you only think that the entrance to the vehicle can be remotely controlled, then tooyoungtoosimple.
With the increasing number of networking functions and near-field communication methods, there are more and more places where cars can be attacked. To break through the defense line of a car, what can I start with? How do car manufacturers and suppliers prevent intrusions? After analyzing the crack cases one by one, the following is a summary. In the summary of the last time, we talked about the way in this year's case, the hackers have used the way to crack the car, and the security problems it shows.
Of course, in the end we said that these attacks and vulnerabilities are not the only ones. What else is there in the car?
In fact, as early as 2011, two research teams from UCSD (University of California, San Diego) and the University of Washington conducted experiments and verifications on the topic of "Comprehensive Analysis of Automotive Security Attacks", from threat types, specific vulnerability analysis, and threat assessment. Three aspects were discussed and experimented separately. In this research report, the main body studied was the ECUs with different functions installed in the car.
Three years later, Charlie Miller and Chris Valasek re-run the work. Their purpose is also to find out if it is possible to start an attack on a car.
If you want to do something good, you must be sharp.
The key to this research lies in the ideas of the two researchers.
The principle that needs to be reiterated is that this attack is still around remote reproducible attacks, and the focus is on the attacks that cause security incidents, that is, the attacks they have launched against Chrysler this year: the steering of the remote control car, Brake or acceleration function allows the vehicle to leave the driver's control and enter an unsafe state. Vehicle stealing attacks such as keys and theft are no longer considered.
The second step is, what do you need to do if you want to get this result?
The most important point is that hackers need to be able to issue commands to these ECUs that control the steering, braking or acceleration of the vehicle, that is, they must get the way to communicate with the vehicle's internal CAN bus, and the CAN bus has more than one line. These core controls The function is at a lower level. A remote attack cannot be directly contacted, so a "bridge" is needed.
This bridge is the batch of ECUs that are not at the core, mostly responsible for receiving and processing radio signals. They all have two characteristics:
1. Ability to accept external information
2. This information may be transmitted to the ECU that controls the core functions via the CAN bus.
Therefore, the idea is to find these ECUs, first black them out, and then use them as springboards to send fake messages to the core function ECU. This kind of ECU can be imagined as a small soldier of the ancient battlefield uploading order. If it can reverse the front and send the false orders given by the enemy, it is also a hand to win.
But this is the ideal state, if it is found to be a false order?
Although the bridge ECUs can send messages to the inside as an entry, this message is not intended to be sent. Between different ECUs, there may be a gateway to intercept illegal messages; on the core ECU, there may be security policy settings, some The action can only be achieved in a specific driving state, or only the specified command. To achieve the goal, or pretend to be legal, then you must know the communication protocol; or bypass the gateway, you need to know the password; or the gateway is also black, let it be used for yourself... and so on.
Therefore, there are three tasks that hackers have to do :
1. Find the entrance to the remote access - the function module with the bridge ECU, such as the car Wi-Fi, OBD, cloud service app in the previous article, including the Bluetooth function synchronized with the mobile phone, the browser and other in-vehicle applications, etc. Etc., all of the external message reception and internal communication functions are possible, and all can be studied
2. Find the communication path from the bridge ECU to the core function ECU
3. Solve all kinds of roadblocks on the communication road
The content of "etc." does not end with the communication module.
The entrance mentioned above, that is, the bridge, plays a role in communication inside and outside. Generally, everyone thinks of the vehicle communication module. But in fact, it doesn't stop there. There are some special-function ECUs that play the same role, but for completely different purposes - ADAS (Advanced Driver Assistance).
Today's ADAS, common such as lane keeping, anti-collision systems, and parking assist technology that is popular with many novice drivers. These functions will eventually ensure that the vehicle is in the lane, to ensure that no collision or collision damage, parking, steering, braking and other functions. There is also ACC, after steering, braking, and automatic acceleration.
That is to say, the ECUs of these ADAS systems will issue commands to the core control function ECU based on the sensor data, and let them work at a specific time, and can also be used as a bridge. Of course, there is no doubt that these systems are designed to aid driving and improve safety, so they are also set to a limited speed. Car companies that may be more cautious will also set up several levels to ensure system functionality.
The reason for mentioning these systems is not that they are not safe, but because they give the hacker a possibility to attack the car. Because of the information interaction with the core control functions, there is a possibility to use them as a bridge to send false messages. What needs to be assessed is how likely this is.
Thus, following this three-step rule, the two researchers began the study.
We know that the CAN bus of the vehicle is a very complicated thing, which will change with the increase and decrease of the technology and function of the vehicle. It is different between different manufacturers, different models of the same manufacturer, and different models of the same model. There will be differences between them. Therefore, they took the 2014 model as the mainstay and selected 13 models. They also selected the 2006 models of these models or the 2010 and 2015 models as comparative studies.
The research mainly focuses on three aspects :
1. How many different entrances exist and the security of the entrance
Some bridge ECUs have the possibility of communicating with the core ECU, but they are small, so they can be considered to have higher security. For example, ADAS can communicate directly with the core function ECU, but there are more security strategies and thresholds. Bluetooth and Wi-Fi communication have lower security due to the distance of action and the ability to implement functions and security policies. If there are more such entries, the level of threats assessed will be high.
2. Vehicle internal network topology
On the one hand, through the different models of the same model to compare and analyze the development of the vehicle's internal network over time; on the other hand, it also wants to verify that the attack on the in-vehicle network is difficult to directly copy because of the huge difference.
Naturally, there is a third purpose, which is to analyze the specific topology to analyze the probability of success of the road passing from the bridge ECU to the core ECU to assess the degree of threat it poses.
3. The opposite of the attack is defense
The attack is not the ultimate goal, the ultimate goal is to better defense. Discover the possible vulnerabilities from the attackable route, which is where you can strengthen your protection.
Different car different life in different years
The final result of this research is very interesting. In their final public research report, they have carried out specific analysis. Because of the limited space, this article cannot be listed one by one. Interested students can go here to see the original text.
For those who are not interested in the specific analysis, let's look at the results together.
They analyzed a total of 21 cars, involving Audi, BMW, GM, Ford, Chrysler, Honda, Toyota, Infiniti, Land Rover and its brand models, mainly in 2014, a total of 13 models, compared to the year 2006 4 models, 3 in 2010 and 1 in 2015. The specific vulnerability level is shown in the following figure (picture from CharlieMiller and Chris Valasek). Only 20 models are listed, and one 2006 Infiniti G35 is missing.
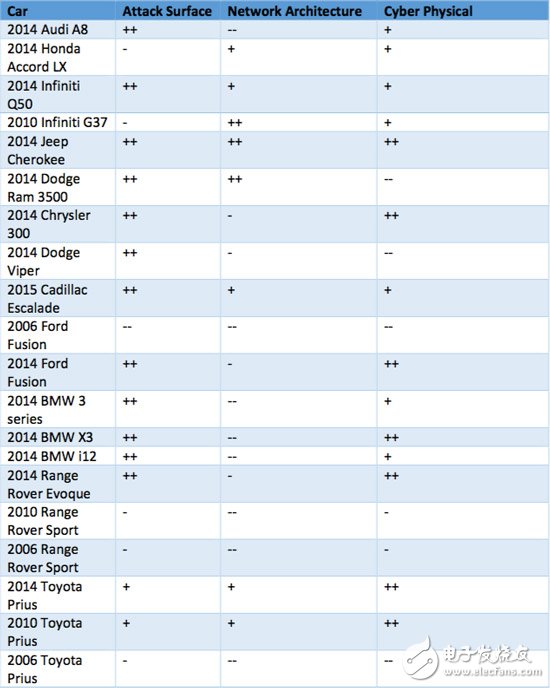
20 models are vulnerable to attack list (from --, -, + to ++, the attack level is increased in turn, the table represents the attack surface, network architecture and core functions from left to right)
From the content of the research, they also got some conclusions:
1. As time progressed, all brand models showed an increase in the number of ECUs. Not only the total number of ECUs, but also the number of bridge ECUs increased significantly. There are two heroes: the development of vehicle networking and driving assistance technology. This means that the possibility of attacking the vehicle and the options available are increasing.
2. The complexity of the network topology of the car is increasing with the increase of ECUs, and more and more network architectures are divided. However, the division of these network architectures is not all aimed at "separating the control core function ECU from other types of ECUs." In the 2014 model, 6 models were not isolated according to their functional importance, and more, although isolated, did not mean that security was high. Because there is no gateway or security boundary after isolation, there is no added security policy, but just a separate separation.
3. Although the internal structure is very different, most vehicles use PC-like technologies, such as browsers and in-car apps. These are things that hackers are familiar with, providing attacks similar to PCs and mobiles. the way
4. Among all the entrances, tire pressure monitoring and keyless entry are the most threatening bridge ECUs by remote attacks.
5. The internal topology of automakers in the same region has a similar structure, which is shown between Japanese cars (Toyota and Infiniti), German cars (Audi and BMW), and American cars (GM and Ford). The two researchers think that it may be because they think about the problem in a similar way, and there is an engineer's job change~
6. Vehicles with these problems do not have OTA function, and the problem can only be recalled. In the end, two rankings were obtained:
1. The easiest to be cracked in the top three: 2014Jeep Cherokee, 2015 Cadillac Escalade, 2014 Infiniti Q50
2. The most difficult to be cracked in the top three: 2014 Dodge Viper, 2014 Audi A8, 2014 Honda Accord
Found a problem? Why did they take Cherokee this year and the roots are here.
Summary :
In fact, the study is not over here. The ambition of the two white-hat hackers is to analyze and get answers for all the models, but the information is not so good, so only these models. Moreover, because they are not all of these models, there is no specific experimental analysis of each car to determine whether dividing more networks can become a barrier for hackers. However, after the results of the research last year, this year, Cherokee began to prove that their research has not stopped, but will continue to move forward.
Micro-probe type NTC mini Temperature Sensor with the properties of sensitiveness and fast response, has been used to rice cooker, electric heater and more others. Temperature range can be from -30°C to 200°C.
Feyvan Electronics designs and manufactures NTC temperature sensors, probes, and cable assemblies for more than 15 years experiences. With excellent long-term stability, high accuracy and short response time properties in high-temperature sensing applications such as automotive, home appliance and industrial use from -40℃ to +250℃, Feyvan electronics provide various choices for a wide range of applications and are available in custom engineered probe package configurations for a variety of mounting and connectivity options with low costs.
Mirco-probe Sensor
Micro-Probe Sensor,Small Temperature Probe,Temperature Sensor,Miniature Sensor
Feyvan Electronics Technology Co., Ltd. , http://www.fv-cable-assembly.com