**Is Face Recognition Really Safe? An iPhone X Perspective on Data Threats**
The introduction of face recognition technology in the iPhone X sparked a wave of excitement, allowing users to unlock their devices simply by looking at them. But as we enjoy this convenience, have we ever considered whether face recognition is truly safe and whether our data is protected at the highest level?
What kind of data security concerns does the iPhone X's face recognition system raise?

At Apple’s recent conference, the iPhone X made headlines with its “bangs†and new features like Face ID, dual cameras, and augmented reality. The device was marketed as defining the future of smartphones, marking a tribute to Steve Jobs and setting the stage for the next decade of innovation.
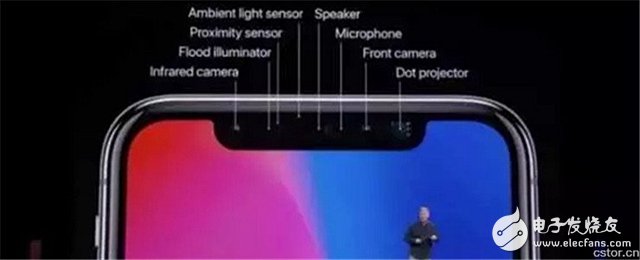
**How Does 3D Face Unlocking Work?**
Face ID is one of the most impressive features of the iPhone X. During the launch, Apple highlighted nine key aspects: facial verification, depth sensing, easy registration, neural network processing, security, natural user experience, privacy, attention-aware unlocking, and integration with Apple Pay. Tim Cook emphasized that the probability of someone else unlocking your phone using Face ID is only 1 in a million—far better than the 1 in 1,000 chance with Touch ID.
Behind the scenes, Face ID uses four of the eight components: an infrared camera, floodlight, ambient light sensor, and dot projector. These work together to create a 3D map of the user’s face with 30,000 sampling points. This data is processed by the Neural Engine in the A11 chip, ensuring secure and accurate identification.
While Face ID has captured public imagination, it has also raised concerns about privacy and data security. Netizens have expressed skepticism, with some joking about anti-face recognition methods. One popular meme even suggested ways to bypass the system.
Senator Al Franken from Minnesota voiced concerns that Apple might collect and potentially leak facial data. He urged Apple to provide more transparency on how biometric data is stored and used. Meanwhile, research from Stanford University showed that deep learning models could infer sexual orientation from facial images, raising further ethical questions about the use of such technologies.
Our analysis using the Qingbo big data monitoring system found that 12.43% of netizens expressed negative emotions about the privacy risks associated with the iPhone X, while 29.5% were neutral. Many remain cautious about the potential misuse of personal data.
**Face Recognition Isn’t Just for iPhones**
iPhone X isn’t the only device using face recognition. Before its release, Samsung’s Note 8 and Xiaomi’s Note 3 already featured 2D face unlock, but these systems were vulnerable to attacks using photos or masks. This led to criticism and poor reviews, highlighting the importance of more advanced 3D face recognition.
Beyond smartphones, face recognition is being integrated into access control systems, surveillance, and payment platforms. Cities like Wuhan have introduced facial recognition for train station entry, while companies like Alipay and JD.com are adopting it for payments. As this technology becomes more widespread, so do concerns about its implications.
**Face Recognition and Data Privacy Risks**
Apple claims Face ID is 20 times more secure than Touch ID, thanks to its 3D structured light technology. However, global data breaches continue to rise. In 2016 alone, over 900 data leaks were reported, with financial theft and account hacking being the most common. In China, the Xu Yuyu case became a symbol of telecom fraud, emphasizing the need for stronger data protection.
Internet companies also collect vast amounts of user data for targeted advertising, raising concerns about consumer discrimination and data exploitation. Personal information is turned into valuable assets, often without users’ full awareness.
**Balancing Technology and Security**
Concerns about data privacy are not new. Germany established the right to data self-determination in 1983, and the EU’s General Data Protection Regulation (GDPR) now gives individuals more control over their personal data. Judicial cases, such as the “right to be forgotten,†have also set important precedents.
On the technical front, researchers are developing countermeasures against face recognition, such as special makeup and anti-face glasses. These efforts highlight the ongoing struggle between technological advancement and individual privacy.
Data privacy is a double-edged sword—it brings both risks and opportunities. Proper protection can enhance services and reduce costs, but the challenge lies in finding the right balance. As technology continues to evolve, it’s crucial for experts across disciplines to collaborate and ensure that progress doesn’t come at the expense of security.
Ultimately, the path forward requires a careful approach—one that respects privacy while embracing the benefits of innovation.
Lenovo Chromebook 300E Gen3,Lenovo Chromebook 300E Keyboard,Lenovo 100e Chromebook Review,Lenovo 100e Chromebook Parts
S-yuan Electronic Technology Limited , https://www.syuanelectronic.com