Green communication: "crime and punishment" of spam
Author: China Telecom Zhejiang company Zhang Jiancheng
At present, the role of advertising is getting more and more attention, which is an inevitable result of the development of commercial society. As the manager of an SP portrays, the mobile user base is becoming a huge market for advertising audiences. At the 3.15 party this year, CCTV made a centralized disclosure of spam messages based on advertising, and showed the audience the industry chain behind mobile advertising, which caused a strong response in the society. From a commercial point of view, this industrial chain is a win-win value chain for all parties, but for the end of the value chain, that is, the majority of mobile phone users, frequent harassment by spam text messages has made them very averse to spam text messages.
The origin of spam
What is spam
A few years ago, people did not have the concept of spam text messages, because the history of mobile phone text messages in China is only about 10 years. And now, as long as the phone is turned on, from time to time you will receive text messages from strange numbers. When you open it, there are those who claim to sell firearms and ammunition, some who sell black cars, some invoices, and many are advertisements. There is no doubt that illegal content such as selling guns, reselling black cars, and selling fake invoices are definitely spam messages. What about the content of advertisements of some companies that are not illegal and not considered spam?
In response to this problem, legal professionals said that messages sent by a client that contain content that violates China ’s laws and regulations or that interfere with the normal life of mobile phone users without the permission of the recipient are “spam messagesâ€. Even if some companies operate legally, they send corporate advertising text messages to users without their permission, which hinders the normal life of the users and belongs to the category of spam text messages.
Sources of spam
With the increasing complaints from users about spam messages, how to resist spam messages has become a focus issue. Generally speaking, the strange text messages received by mobile phone users mainly include the following:
(1) SP (Value-added Service Provider) promotional message;
(2) Commercial advertising short messages sent by merchants through the "Enterprise Information Communication" method;
(3) Peer-to-peer text messages sent through mass senders and mass sending software, including ordinary commercial advertisements, as well as a large number of gray industry advertising short messages and fraud-type short messages.
The text messages sent by the SP were once the focus of user complaints, but the topics discussed were charging traps and suspected fraud. After unified rectification, the industry has issued some regulations, and these types of problems have obviously improved.
As an industry application, "enterprise communication" is now quite common. Most of its users are units, enterprises and merchants, and some are of the advertising nature. The former is generally more standardized. In addition to sending text messages from internal business groups, the promotion of external text messages is basically within a limited range. For example, banks and securities companies should send text messages such as new wealth management products, new stock purchase notices, risk reminders, etc. to their customers. It should be a relatively reasonable business behavior. The frequency of text messages is not high, and they will not be flooded. However, there are some "Corporate Communication" users of the nature of advertising operations. The business they undertake is to send promotional messages to the businesses in need. Because of the survival of the mass-sending business, naturally the more text messages are sent, the better the business is. one. What these advertisers rely on is the ability to provide different mobile phone target customer groups according to different types of publicity services.
Using mass sender and mass sending software to send through one or a group of mobile phone numbers, you can send thousands to tens of thousands of short messages in a few minutes. Because the delivery method is simple and easy to use, many merchants also choose it as a means of commercial promotion. There are also so-called "short message group sending companies" on the market, specializing in sending text messages for other people to make a living. However, many merchants or "mass sending companies" do not have a targeted mobile phone number group, and inevitably send the entire number segment aimlessly, and mobile phone users often receive some text messages that are not related at all. In particular, a large number of text messages from gray industries are often used in this group because of the risk of content being traced.
Compared with mobile phone text messages, PHS has fewer spam text messages and fewer related complaints. There are about 90 million PHS users in the country so far. Although the absolute number is quite large, there are several factors that prevent PHS from becoming the main target of spam. First of all, PHS numbers use the same bit length as ordinary fixed-line numbers, and it is not easy for non-professionals to distinguish which numbers are PHS and fixed telephones; and mobile phone numbers have obvious characteristics. Second, PHS does not implement off-site roaming, which is limited to local use. The scope is relatively small, and it avoids the situation of being registered and tracked in off-site locations; and mobile phone users will immediately receive a lot of local advertising short messages when they go outside. Third, the opportunity for PHS to register as a contact phone is relatively small compared to mobile phones. Third parties collect user data through industries such as banking, insurance, medical care, and public services. PHS numbers are generally relatively small. Fourth, PHS sells through social cooperation channels much less than mobile phones, and the chance of leakage of user information is relatively small. The dangers of spam
The harm of spam messages mainly includes the following aspects:
(1) Affect rest. At present, there are a lot of mobile phone users who turn on the phone all day. If they receive a spam message during the lunch break or even in the middle of the night, it will affect the quality of the rest, and it will be unhealthy for a long time.
(2) The content of SMS involves a lot of scams, and the contents of frauds such as winning prizes and falsely claiming that credit cards are consumed are endless, which is unpredictable. There are a lot of reports involving fraudulent messaging across the country, which has caused great economic losses to individuals.
(3) The sale of fake invoices, counterfeit documents, underground money houses, and the sale of black cars and black guns in the content of text messages disrupted social order and endangered public order.
Discussion on Anti-Spam SMS
Improve personal information security and legal system
The work of anti-spam SMS requires the participation of the whole society. Now mobile phone user information may be leaked at any time. A company can grasp the mobile phone number information of about 300 million users nationwide, which makes people feel uneasy and worried. In some countries, the user's address and phone number are absolutely private information and cannot be disclosed casually. Our country should further improve the legal system, strengthen the implementation, fundamentally protect the confidentiality of user information, and strictly pursue and crack down on the trading behavior of buying and selling user information. Driven by business interests, morality alone cannot serve as a constraint.
In addition, for spam messages, the country also needs to improve other laws. In countries such as the United States, the United Kingdom, and Germany, there are relatively strict rules for sending commercial promotional text messages, and some even require the prior consent of the recipient. In our country, as a new medium, SMS has achieved rapid development at the beginning of this century. The previously enacted laws need to supplement the provisions for new things. At the same time, China's "Telecommunication Regulations of the People's Republic of China" was released relatively early. It was impossible for the text message issue to enter the legislators' eyes when this administrative regulation was formulated. It is recommended that SMS should be regulated as a general public communication method.
Strengthen the responsibilities of operators
The operator is an important part of anti-spam SMS, because the network is the carrier of the SMS service, and the operator has the complete user mobile phone number. But operators also have difficulties in managing spam messages.
(1) Difficulties in the management of spam messages
At present, the main difficulty in managing spam messages is spam messages sent by peer-to-peer (through mass senders and mass sending software). Because personal mobile phone numbers are used for sending, user reports are relatively scattered, and because many prepaid brand mobile phone numbers are available everywhere, the owner does not need to register user information in detail (the real-name system has not yet been adopted), so it is difficult to process and trace the source. Some people who take advantage of the situation use fake ID cards, buy post-paid mobile phone services in the fictitious name of employee group purchases, etc., and use these numbers to send point-to-point text messages in turn, sending huge amounts every day until the down payment next month.
(2) Technical measures to strengthen plugging
In addition to strengthening the review of mobile phone network access, the technical means of governance is to monitor daily SMS traffic, establish the necessary support system, and closely monitor the sending of abnormal SMS. First of all, we must sort out the credit status of current customers and add whitelists to some high-quality customers who usually use a large amount of text messages. For ordinary numbers, the number of short messages sent per unit time exceeds a certain threshold, and an early warning program is started immediately. The program judges the network access time of the number, account credit, etc. Numbers with poor credit or new network access are listed as high alert levels, and the transmission of these numbers is blocked according to actual needs to control risks and effectively reduce the mass distribution of advertisements.
Some operators' short message center systems have some of the above identification restriction functions. To improve the monitoring, filtering, and analysis functions, it is recommended to set up a special monitoring system, as shown in Figure 1.
Figure 1: Schematic diagram of short message traffic monitoring
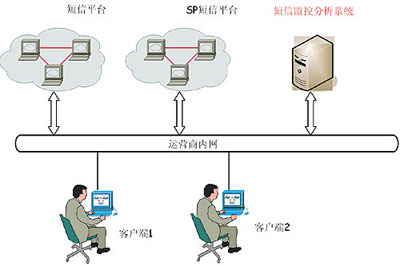
The upper right of Figure 1 is a set of SMS CDR analysis system. It consists of several parts: A, bill collection process; B, bill sorting program; C, bill record database; D, abnormal bill analysis program; E, white list management; F, alarm processing module; G , Business interface, etc. This system is the basis of abnormal SMS monitoring work. The working principle of each module is shown in Figure 2.
Figure 2: Schematic diagram of the functional modules of the SMS monitoring and analysis system
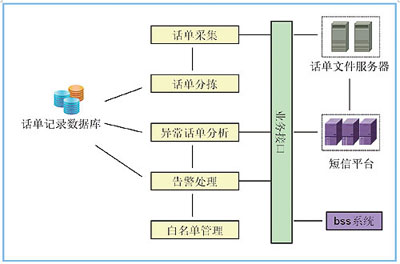 The design of the bill collection process is a 24-hour uninterrupted real-time collection program, which is responsible for collecting the instantly generated SMS bills from the SMS platform for subsequent sorting work.
The design of the bill collection process is a 24-hour uninterrupted real-time collection program, which is responsible for collecting the instantly generated SMS bills from the SMS platform for subsequent sorting work. The sorting of SMS bills is to separately process and store different types of bills according to the established rules. For example, according to the object of SMS sending, it is divided into PHS, mobile phone, and Unicom mobile phone. According to the region where the SMS is sent, it can be divided into XX provinces and XX regions. When judging where the number belongs, PHS can use the area code, and mobile phone numbers of China Unicom can be subdivided against the H code table. In the design, the sorting rules can be defined finer and richer according to the actual needs.
The SMS bills after sorting are stored in each table of the database according to certain rules, and there are both classification differences and mutual relations between the tables. Every day's SMS bill records have original time stamps. When you need to count certain types of bills in a certain period of time, you can get them from the database table. According to the storage space of the database server, we can set the maximum storage time of the bill, such as three months, half a year, one year or more.
The final work we care about is in the analysis phase of the abnormal transcript. With the bill sorting step, bill storage becomes more organized, and bill analysis is easier. In conjunction with the work of anti-spam text messages, special attention must be paid to the calling number with a large number of senders, because operators generally do not stipulate the upper limit for users to send text messages. It can be counted every 10 minutes, and the number of SMSs sent by a single number on that day exceeds 500 (for example) as the first warning threshold, and more than 800 as the second warning threshold. First of all, add the number of the province and the number of the extranet that exceed the first warning threshold to the suspicious list; then remove the whitelist number (the first filter) from the number of the province's own network; then check the network time and account credit information through the interface Wait, sort out the numbers with bad credit or the time to access the network within one month (second filtering) are also included in the suspicious list, and the list is displayed on the alarm interface. When the cumulative sending number of these suspicious numbers exceeds the second warning threshold, a blocking operation request is immediately sent to the SMS center through the interface.
Among them, the threshold value is set with certain empirical judgment, which can be adjusted as needed. In the past, we found that a single number sent a lot of thousands or tens of thousands in a short period of time. In order to prevent these numbers from being sent in time, you can adjust the frequency of statistics refresh, such as every 5 minutes. In addition, although the transmission volume of some single numbers is not very prominent, they appear in the form of serial number groups (number basic serial numbers), and the cumulative transmission can reach tens of thousands or more than one hundred thousand, and these numbers should be treated first.
The purpose of setting up the white list is very clear, that is to protect the credit customers who usually send a large amount of text messages from accidental injury by restrictive flow measures.
The alarm processing module is responsible for compiling suspicious numbers into alarm information and presenting them on the monitoring interface, and classifying the alarm levels according to the situation.
The system has several important interfaces. First, the interface with the SMS bill storage server is used to collect and generate bills in real time. Second, the interface with the bss system is used to query the basic information such as the number of network access time and account credit records. Third, the interface with the SMS center. When the number of suspicious numbers sent by SMS exceeds the limited alert value, the interface is used to send a blocking operation instruction to the SMS center; when the blocking period expires, an unblocking operation is sent through the interface instruction. The above restrictions are appropriately relaxed during important holidays, depending on the situation, because of the phenomenon of mass blessing text messages.
It should be noted that the above suspicious numbers may also contain non-spam messages sent by normal users, and these users can be added to the white list after verification. The operator must make the necessary explanation to the user for possible misoperation and seek the user's understanding. Ultimately, the basis for judging spam messages must be checked, but strictly speaking, this is not something that operators can do.
(3) Regulatory system restrictions
The Constitution of our country stipulates that citizens ’communication secrets are protected by law. Unless the national security or criminal investigation is required, public security organs, national security organs, or people ’s procuratorates shall inspect telecommunications content in accordance with the procedures prescribed by law. No organization or individual may Check the telecommunications content for any reason.
Therefore, according to the above regulations, telecommunications companies do not have the right to check the content of short messages sent by users to verify whether they are spam short messages. This makes the current anti-spam practical work into an embarrassment, because the information will be transferred to public security and other departments for inspection, and the feedback from law enforcement departments will take some time, and the timeliness of processing spam messages will be lost. Therefore, it is still practically difficult for operators to contain spam messages completely.
Electrical Cable is in any building requiring electricity for the lighting and power. There are many types of cable used to keep a device running, choosing the right type and size of cable is critical. Any cable installations need to be fully tested by a suitably qualified professional.
There are many different kinds of cables in the market; yidashun produces Data Cable, ac Power Cable, DC Cable and Computer Cable mainly. Cable is the key to connect different devices to make it work normally. Without it, many devices can`t work, the world would be dark.
If you want to find the cable for you phone,computer, laptop Adapter , printer, projector, or scanner etc, you can contact with yidashun, we can make the cables you need, and also can support you with factory competitive price, and also good quality.



Cable
USB Cable,Lighting Cable,Micro USB Cable,Iphone Cable
Shenzhen Yidashun Technology Co., Ltd. , https://www.ydsadapter.com